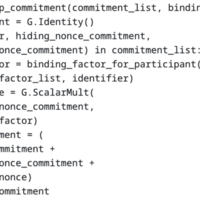
Speeding up FROST with multi-scalar multiplication - Zcash Foundation
by Deirdre Connolly, Conrado Gouvea We optimized our implementation of FROST by upwards of 50% over the trivial implementation, without changing the protocol and therefore maintaining its existing security guarantees. We use a known trick to do so: multi-scalar multiplication, which is exactly desi…